🎅 SantaStealer: Inside a New MaaS Information Stealer Targeting Credentials, Crypto, and Digital Assets
Published by: Eclipse Intel Threat Research Team (ETRT)
Date: December 24th, 2025

Executive Summary
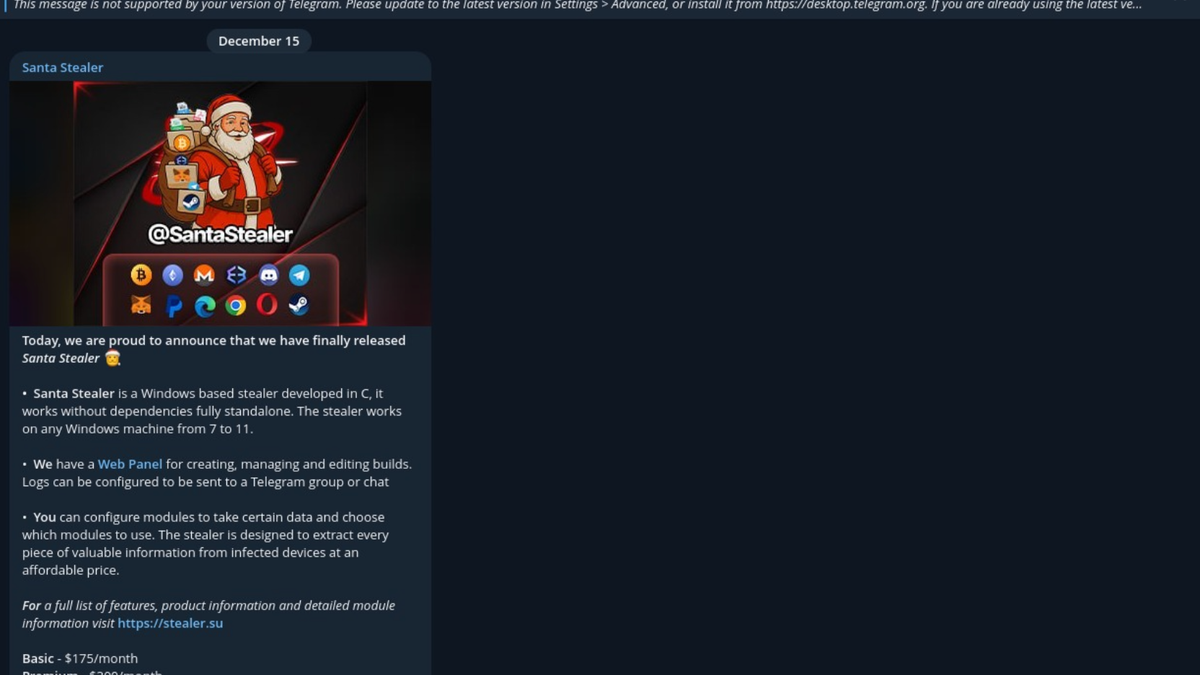
In December 2025, the Eclipse Intel Threat Research Team identified a newly emerging information-stealing malware dubbed SantaStealer, actively advertised and sold across underground cybercriminal ecosystems. Operating under a Malware-as-a-Service (MaaS) model, SantaStealer significantly lowers the barrier to entry for cybercrime by enabling low-skill actors to deploy credential-stealing malware at scale.
SantaStealer is assessed to be a rebranded and repackaged variant of BlueLine Stealer, refreshed with new branding, a modern web panel, Telegram-based promotion, and subscription-based pricing tiers. While current observed samples appear relatively basic, its commercialization trajectory suggests rapid evolution, feature expansion, and broader adoption in the near term.
Key Takeaways for Defenders
- Low cost + MaaS delivery = high abuse potential
- Targets browsers, crypto wallets, and messaging apps
- Telegram used for advertising, log delivery, and operator coordination
- Likely to appear in phishing, cracked software, and ClickFix campaigns
- Early-stage threat today — high-volume threat tomorrow
Overview of SantaStealer
SantaStealer is a Windows-based information stealer designed to harvest sensitive user, system, and application data from infected hosts. It is marketed as a turnkey solution for cybercriminals seeking fast monetization via credential theft, financial fraud, and access resale.
Observed Characteristics
- Malware-as-a-Service (MaaS) subscription model
- Tiered pricing (Basic / Premium / Lifetime)
- Active promotion via Telegram channels and underground forums
- Web-based management panel for builds and log retrieval
- In-memory execution to reduce disk artifacts
By offering an end-to-end operational ecosystem, SantaStealer mirrors the growing professionalization of cybercrime, where malware is sold like SaaS products.
Data Theft Capabilities
SantaStealer supports broad data-collection functionality focused on high-value assets.
Browser Data
- Stored usernames and passwords
- Cookies and active web sessions
- Browsing history
- Saved credit card information
Cryptocurrency Assets
- Software-based wallet data
- Browser extensions linked to crypto platforms
- Private keys and wallet artifacts
Application Credentials
- Telegram
- Discord
- Steam
System & User Artifacts
- Local files and documents
- Screenshots captured from infected systems
- Clipboard contents
- System metadata and language settings
Data Exfiltration Workflow
Once collected, stolen data is:
- Aggregated locally
- Compressed into ZIP archives
- Exfiltrated to attacker-controlled C2 servers
- Transferred in ~10 MB chunks to evade detection thresholds
This segmented exfiltration approach allows the malware to blend into normal network traffic and bypass basic monitoring controls.
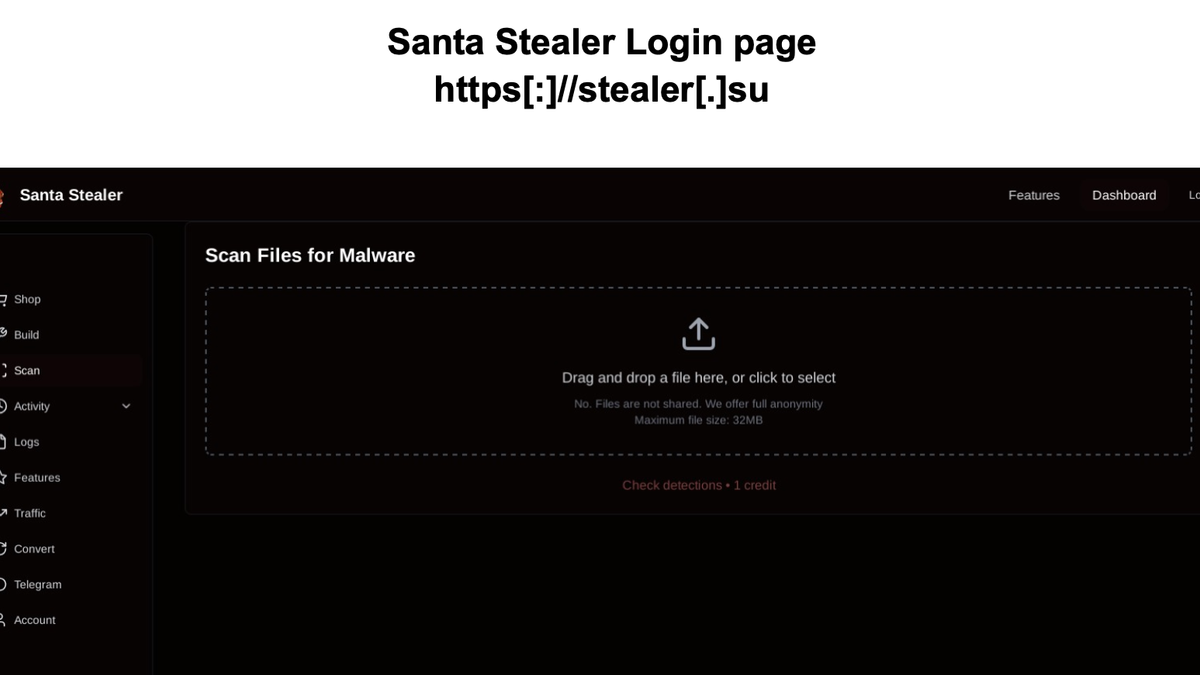
Infrastructure & Operator Panel
SantaStealer operators are provided with a dedicated web-based control panel, hosted on attacker-owned infrastructure:
- Login Portal:https[:]//stealer[.]su
- Features include:
- Build generation
- Log management
- Module configuration
- Telegram integration for notifications
The presence of a polished panel indicates intent for long-term operation, not a one-off malware release.
Distribution Methods & Initial Threat Assessment
While SantaStealer has not yet been observed in mass exploitation campaigns, Eclipse Intel assesses the following likely distribution vectors based on stealer tradecraft:
- Phishing emails with malicious attachments or links
- Cracked or pirated software bundles
- ClickFix-style social engineering, tricking users into executing malicious commands
- Trojanized installers and fake software updates
Assessment:
Current samples show limited obfuscation and are detectable by modern defenses. However, MaaS operators historically iterate rapidly. Expect future versions to include:
- Better AV/EDR evasion
- More modular loaders
- Improved persistence mechanisms
Eclipse Intel Perspective
SantaStealer is not yet a headline-grabbing threat — but this is exactly the phase where defenders should pay attention. Nearly every major stealer family started as a “low-noise” MaaS offering before scaling into mass exploitation.
At Eclipse Intel, we track early-stage malware commercialization, underground marketing signals, and threat actor infrastructure — helping organizations detect threats before they reach widespread abuse.
Intelligence beyond the surface.