Inside the Knownsec Leak: Malware Source Code, C2 Frameworks & Global Targeting Exposed
Eclipse Intel Threat Research Team (ETRT) identified a GitHub repository (now removed) hosting a major leak of internal data belonging to Knownsec, a well-known Chinese cybersecurity and intelligence-linked organization.
The exposed archive contained ~12,000 internal documents, including:
- Malware and Trojan source code
- Command-and-Control (C2) frameworks
- Exploits and vulnerability research
- Internal project reports
- Global targeting lists
- Nation-specific sensitive data collections
The breadth and sensitivity of the material provide rare insight into the operational tool set, data collection scale, and targeting priorities associated with Chinese cyber operations.
Overview of the Exposed Data
Scale of the Leak
The exposed database includes around 12000 documents. The preliminary analysis of the exposed data includes project documents, source code of malware, command and control framework (C2) and exploits.
Global Targeting Across Asia, Europe & Africa
The target list expending across Asia, Europe and Africa. The list also specifically lists of countries like India, Japan, Indonesia, UK and Vietnam.
Notable Breach Details Found in the Leak
The exposed Knownsec archive includes extensive nation-state data, including a 95 GB compressed file comprising Indian immigration information and digital infrastructure maps. Other notable breaches included 3TB of South Korean telecom data and 459GB of Taiwanese road planning data. We also identified an Excel file containing a list of various data breaches along with the number of records and available data fields.
Two other screenshot is attached below that lists the files in a directory. Listing various databases from countries like India, Taiwan, and Vietnam (the countries' names were identified based on the country code present in the file name).
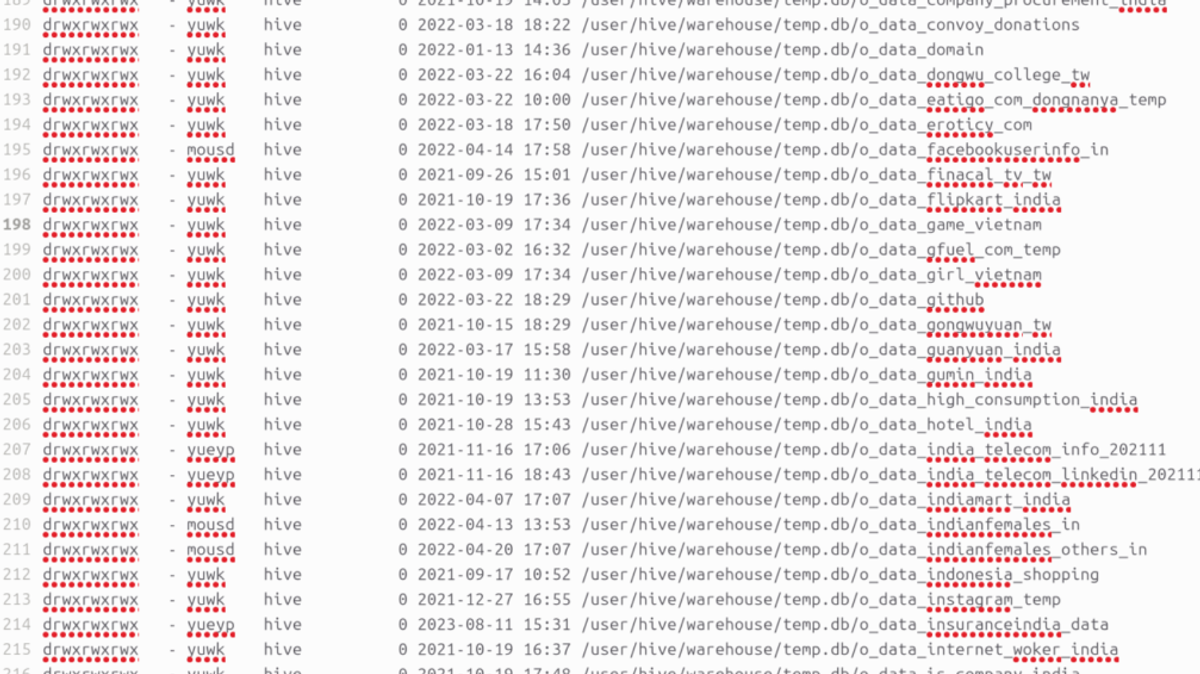
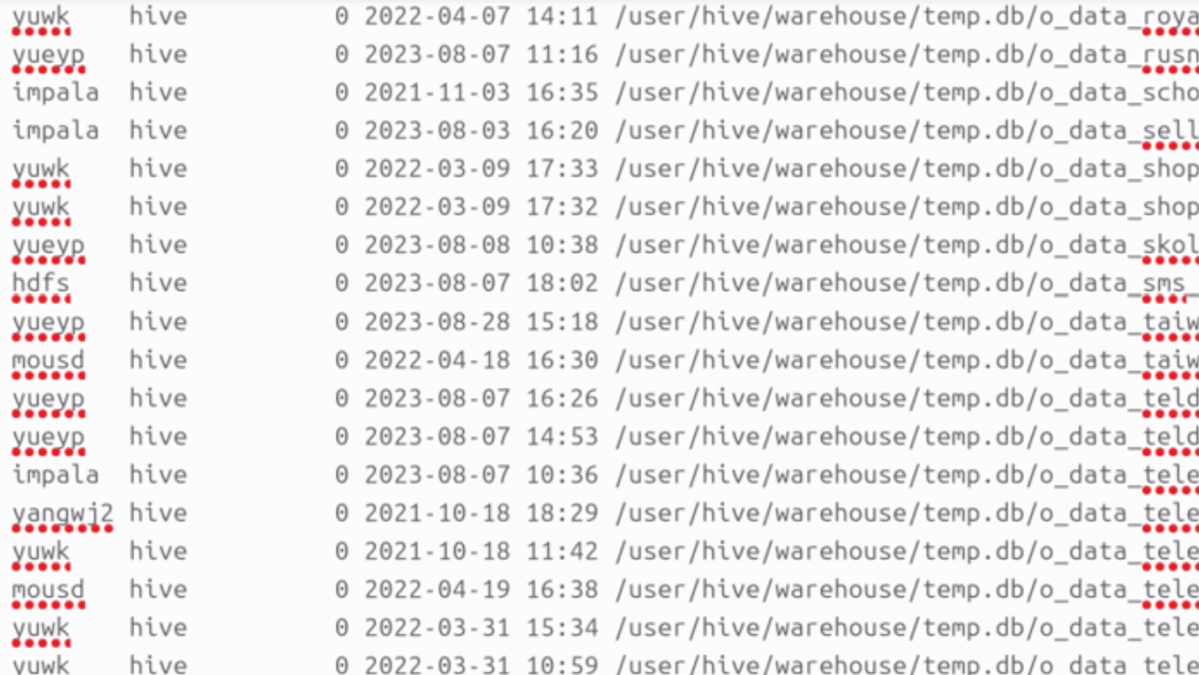
Image 2: Directory list and available database names
The notable database from the above lists named “o_data_royalenfied_india” (possibly misspelled) is affiliated with the Indian automobile company Royal Enfield. Another database is linked to the e-commerce platform Flipkart. Along with various other Indian databases.
These data collections indicate long-term, structured intelligence gathering, not opportunistic breaches.
Exposed Tools & Capabilities
ZoomEye — Internet-Wide Scanning & Reconnaissance Engine:
ZoomEye is China’s equivalent of Shodan/Censys.
The leaked documentation highlights capabilities such as:
- Filtering for vulnerable device IPs
- Large-scale scanning operations tied to offensive campaigns

Image 3: Zoomeye
The screenshot attached below document mentions 100,000 vulnerable VPN appliances affected by an “undisclosed vulnerability", proving that the tool is capable to Identifying exposed enterprise assets.
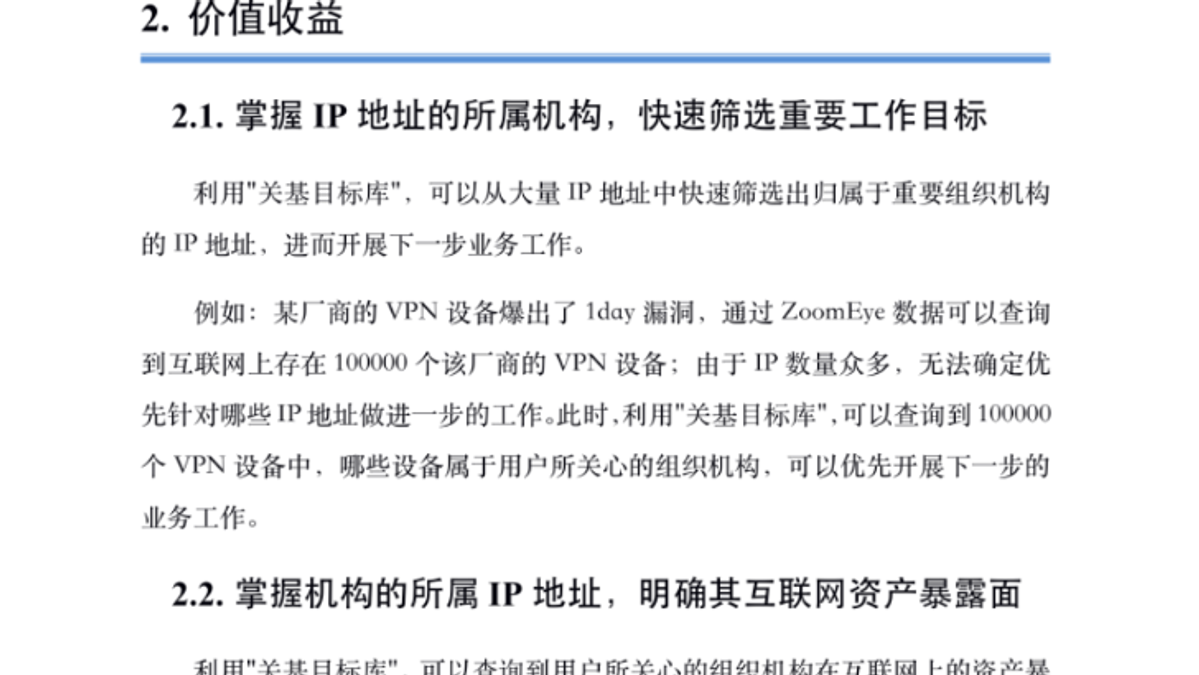
Image 4: Documentation related to Zoomeye
Windows Remote Access Trojan (RAT):
The archive contained detailed documentation and source components of a Windows RAT supporting:
- File browsing
- Process management
- Screen monitoring
- Keylogging
- User activity monitoring
- Remote execution
The document also described evasion capabilities against:
- 40+ antivirus engines
- Firewalls
- User Account Control (UAC)
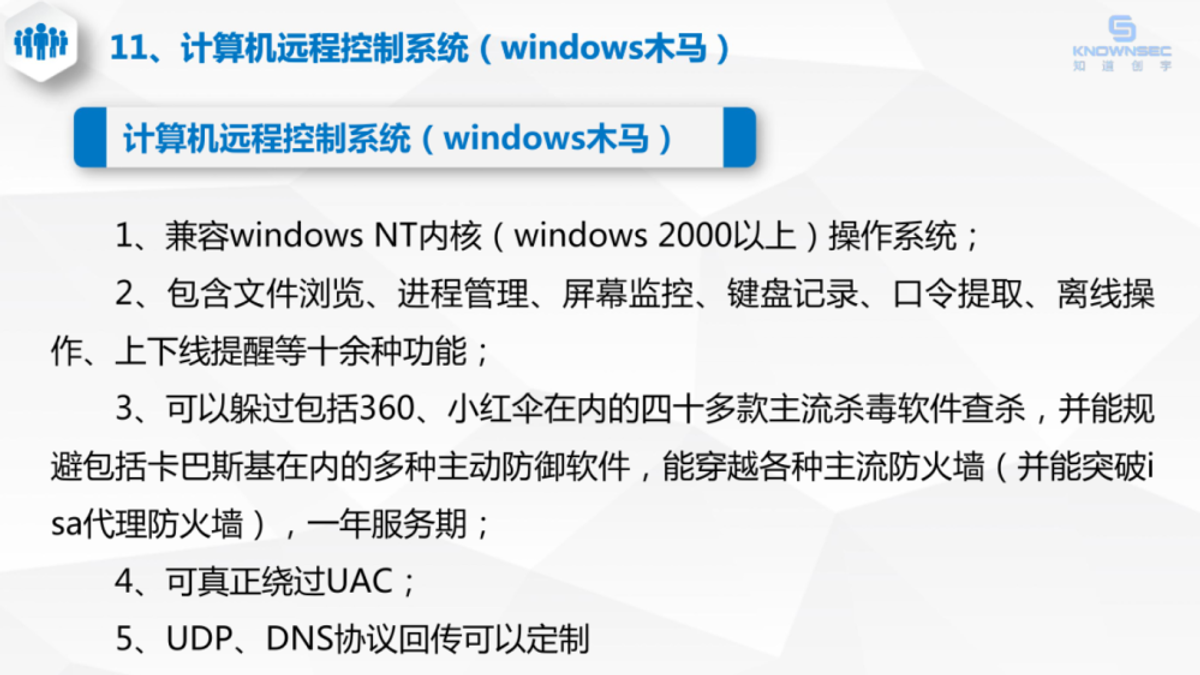
Image 5: Document showcasing Trojan capabilities
KRACK Attack Documentation
The leak included internal documentation associated with KRACK (Key Reinstallation Attack) — targeting WPA2 Wi-Fi networks.
The document outlined:
- Attack flow
- Vulnerable protocol components
- Internal testing notes
- Target environment suitability
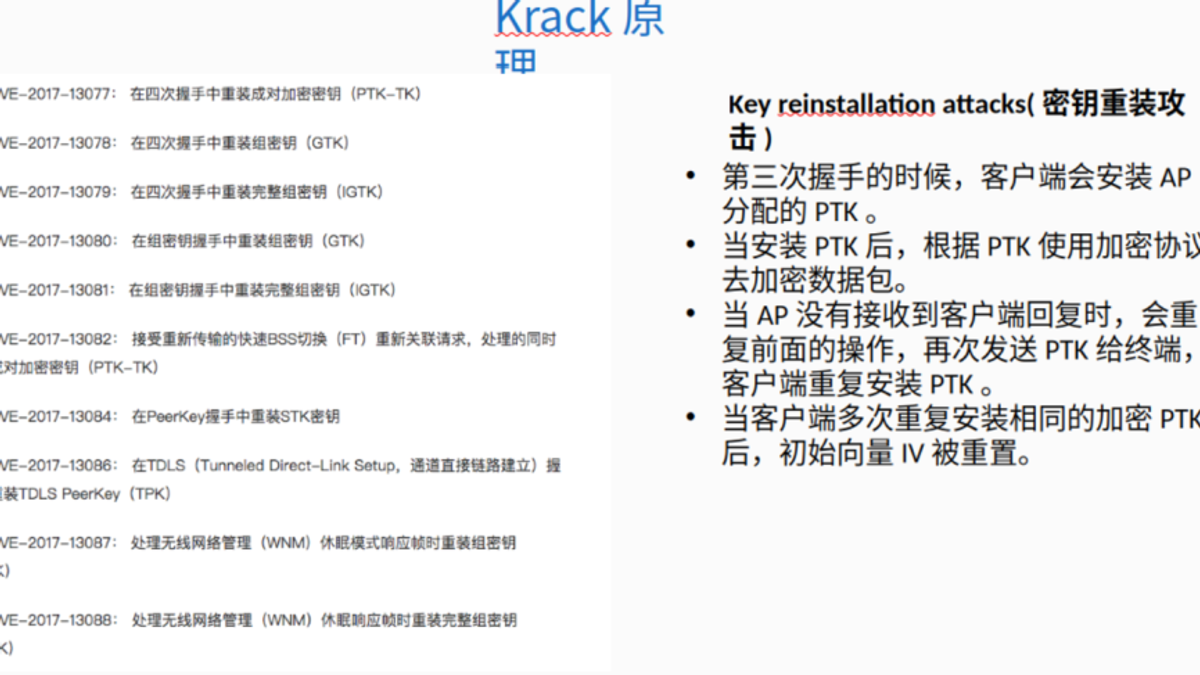
Image 6: Document showing details of Krack attack
Assessment
The Knownsec leak provides rare visibility into Chinese cyber operational tooling, reconnaissance capabilities, and structured targeting.
Although the GitHub repository was live only briefly, the exposed material validates:
- Nation-state level targeting across Asia, Africa, and Europe
- Advanced scanning and reconnaissance infrastructure
- Custom malware and RAT capabilities
- Extensive foreign data harvesting
- Structured intelligence-gathering operations
This exposure acts as a critical reminder for impacted nations — especially India, Taiwan, Japan, Vietnam, and European regions — to strengthen national cyber defenses and monitoring of data exfiltration pathways.
Conclusion
The Knownsec leak represents one of the most revealing snapshots into Chinese cyber capabilities discovered publicly.
Although the dataset was available only for a short time, it exposed:
- Nation-specific sensitive data
- Malware and C2 development artifacts
- Reconnaissance infrastructure
- Global targeting intelligence
For governments and organizations in the affected regions, this leak underscores the need for robust cybersecurity investments, continuous threat intelligence monitoring, and proactive national security measures.